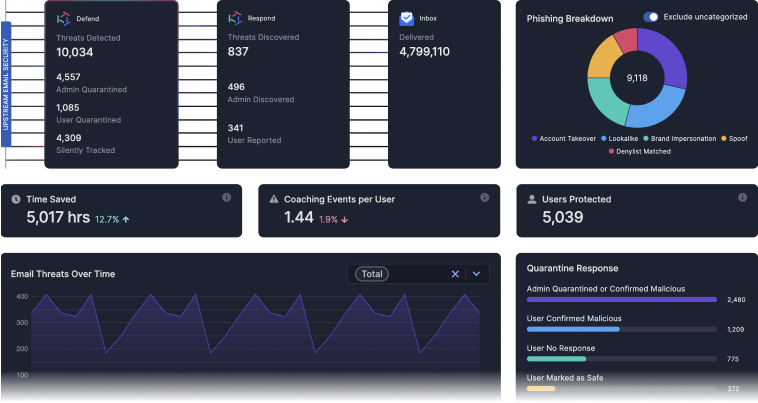
Complete
Cloud Email Security
An AI-based approach to defending against advanced phishing threatsand protecting sensitive data on email.
Trusted by global industry leaders
-
Email-based threats are the #1 concern for security leaders
-

250,000+
BEC incidents reported to the FBI since 2013 -
$4.5M
Average cost per breach of Phishing and BEC attacks -
65%
of infosec experts say email stores the most IP, PII & PHI
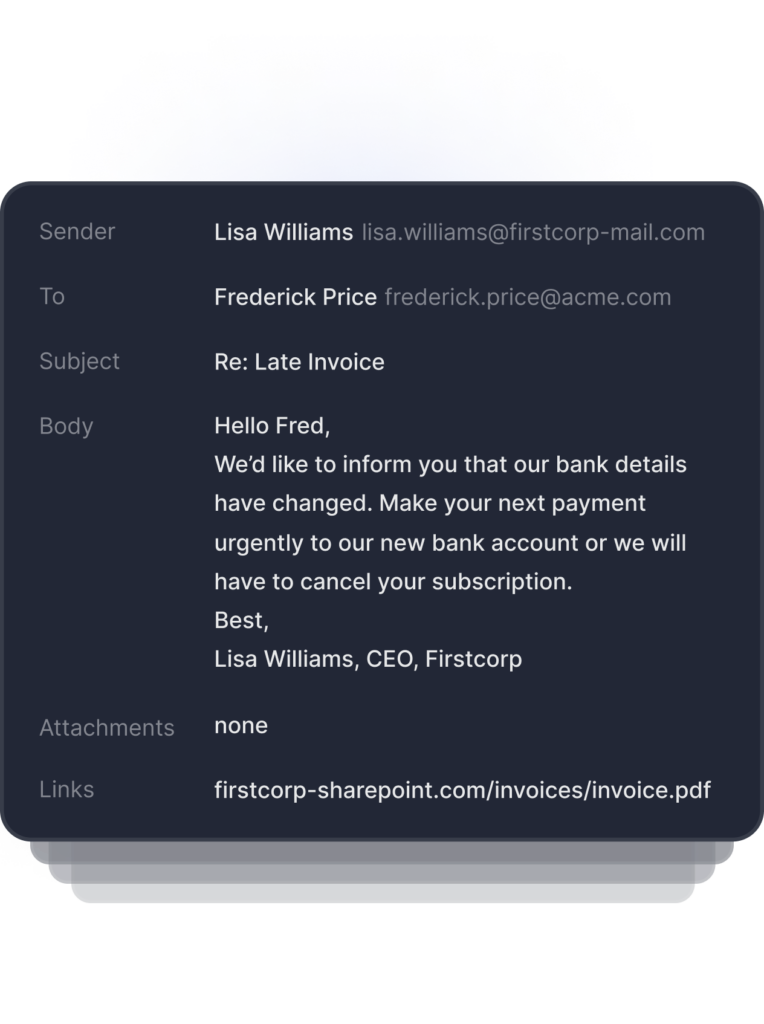
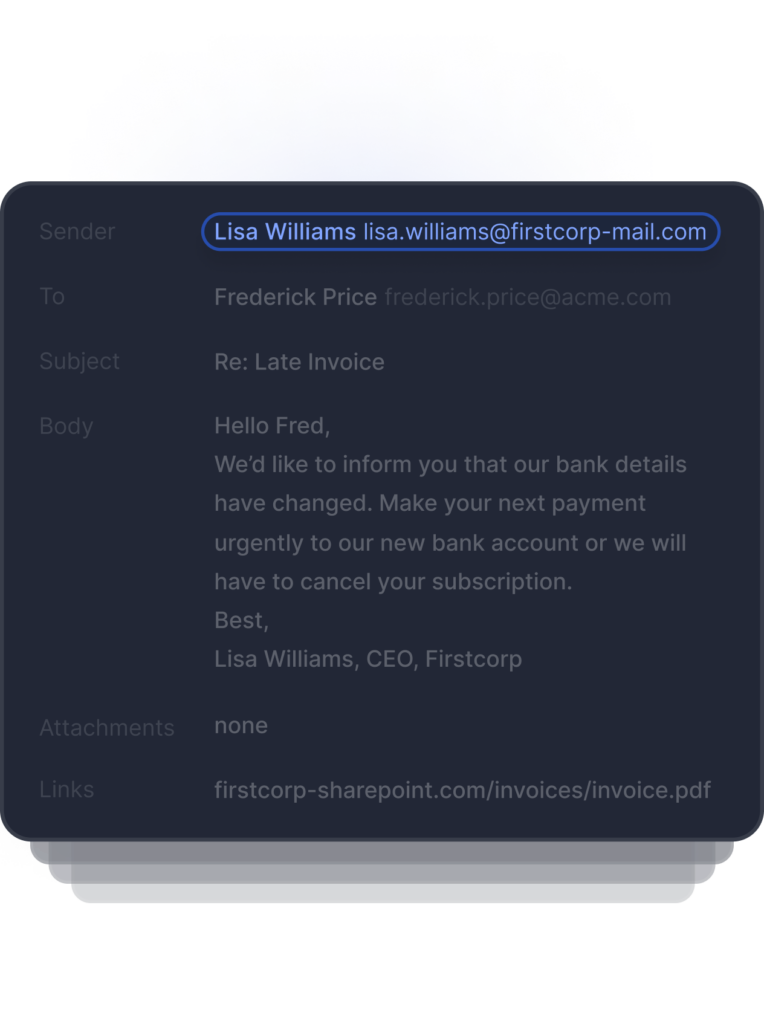
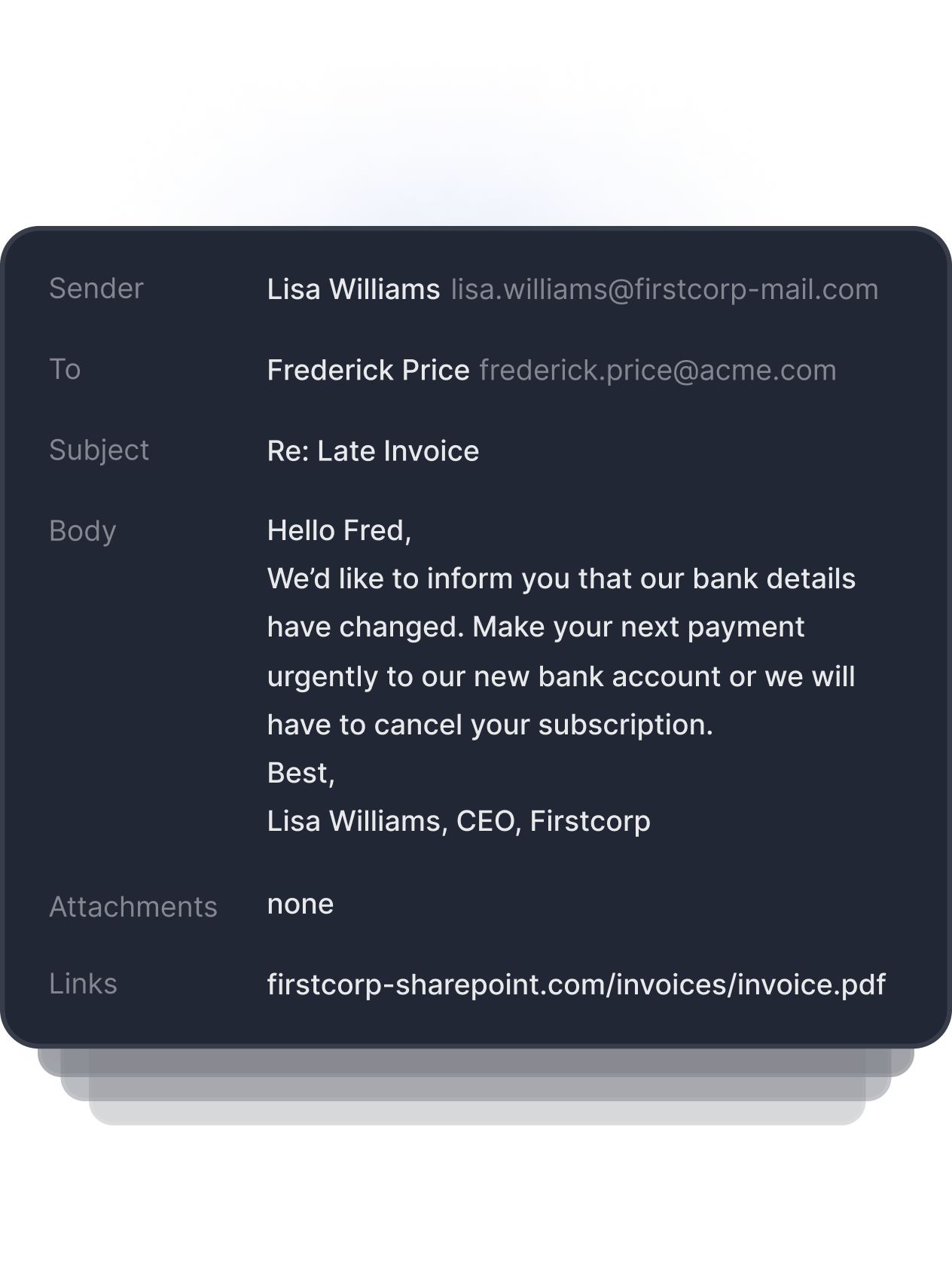
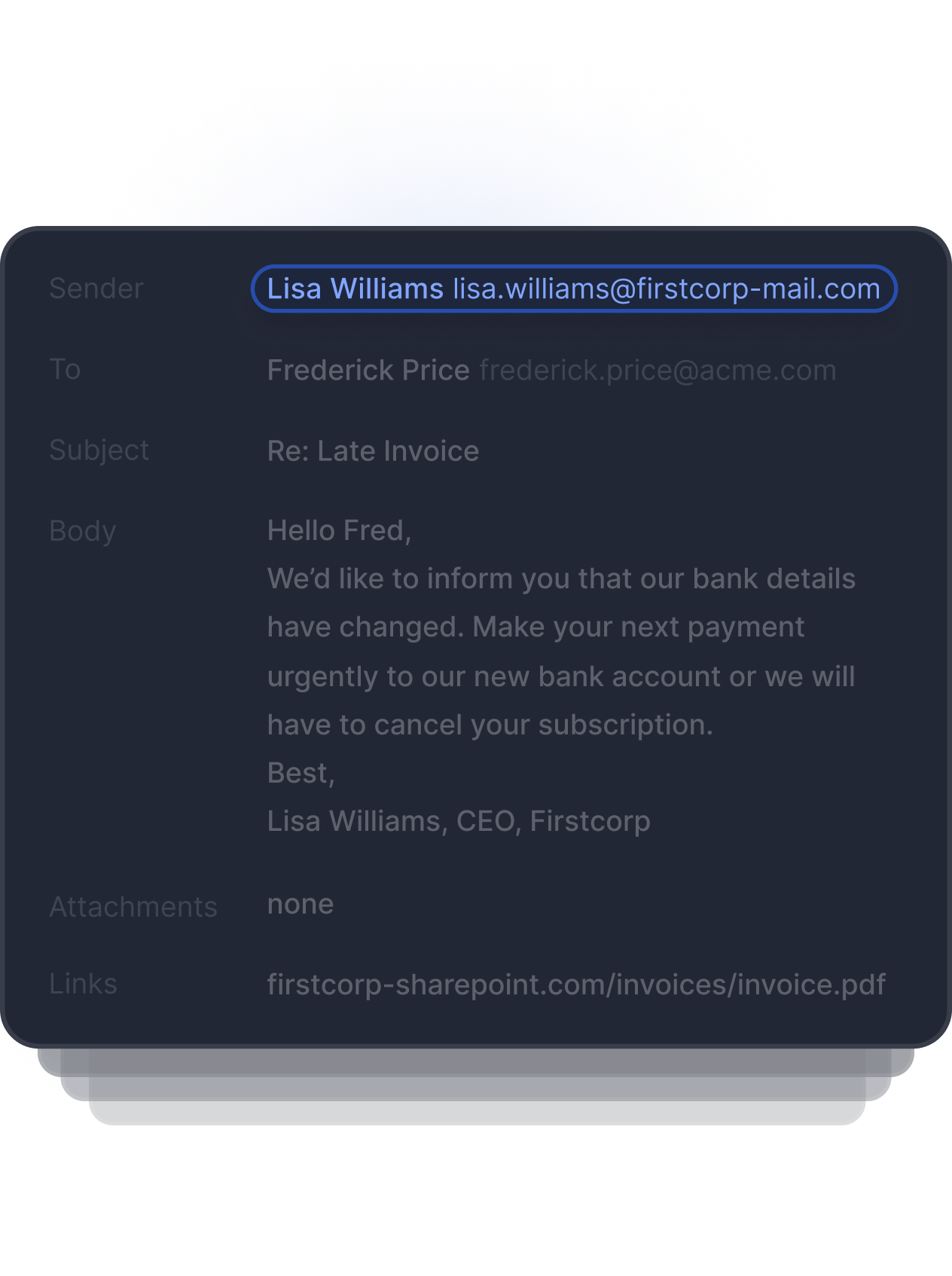
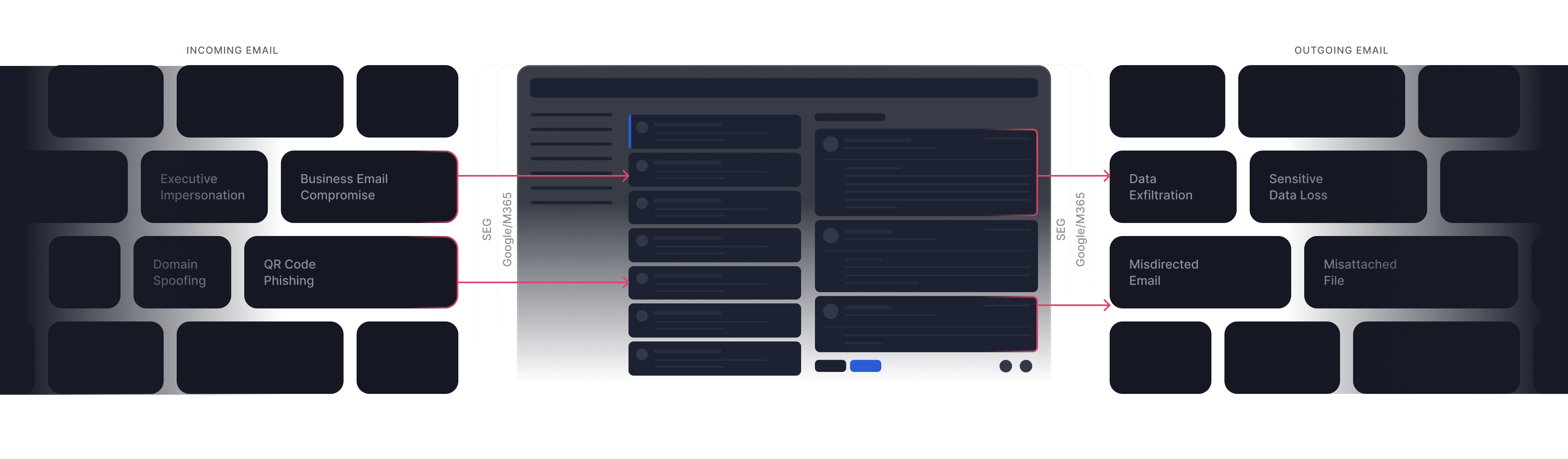
Advanced email threats bypass existing security
Tessian stops sophisticated email threats like BEC, ATO, and impersonation attacks that leverage modern tactics and procedures which bypass traditional email security controls.
“Tessian detects email impersonation and account takeover attacks, while protecting us from advanced threats that traditional email gateways miss.”
Tessian stops
advanced email threats
Tessian uses behavioral analysis and artificial intelligence to detect and prevent email based attacks.
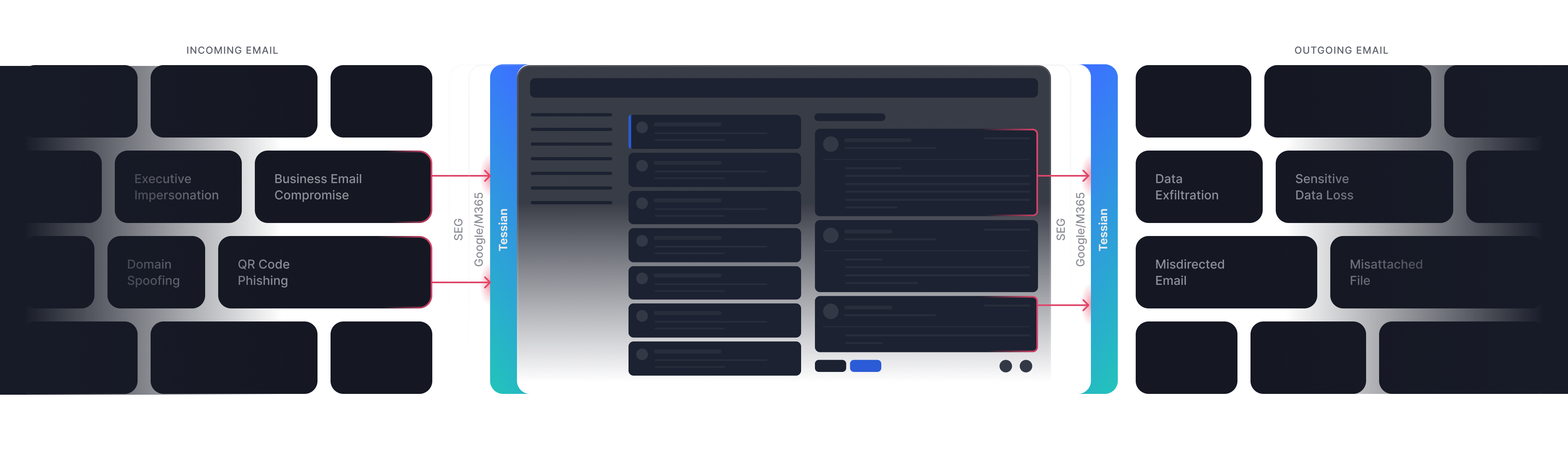
How Tessian’s AI works
AI based threat detection
Tessian AI Explained
Tessian uses an ensemble of AI based approaches because it's the only way to defend against advanced phishing attacks, and protect against sensitive data loss on email. Through behavioral, content and threat network analysis, Tessian AI automatically adjusts as our customers hire, acquire, and adapt.
AI based threat detection
Behavioral Analysis
Tessian AI uses millions signals to identify normal behavior vs. anomalous activity. Tens of thousands of historical events are used to build a strong behavioral baseline for each user.
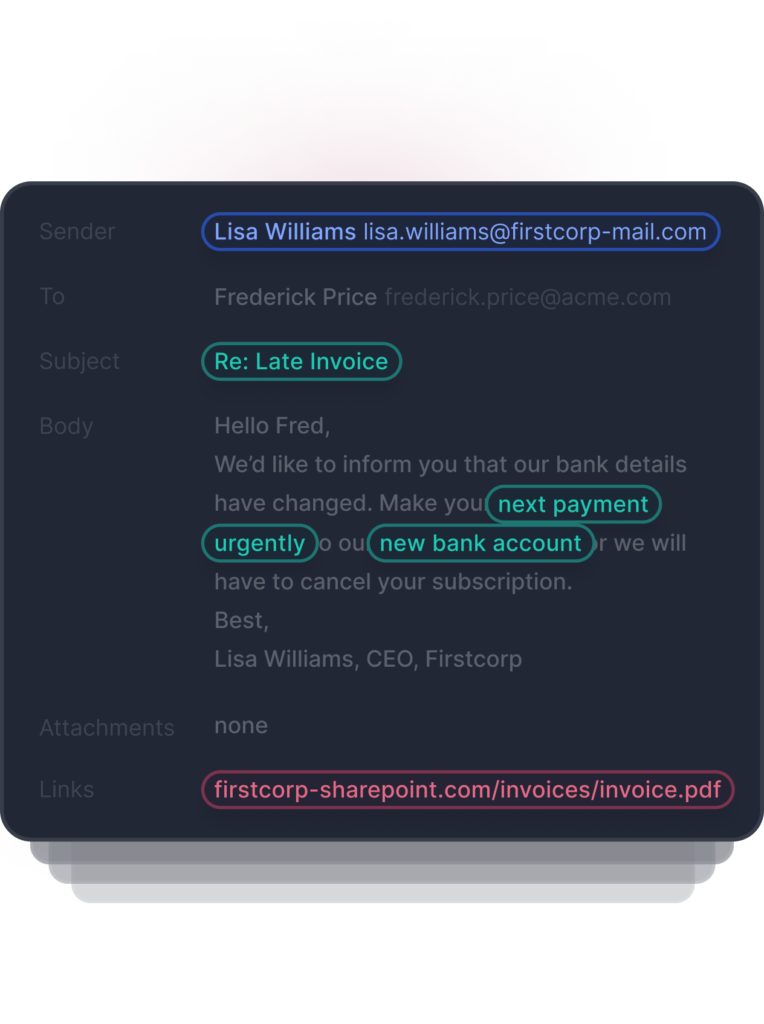
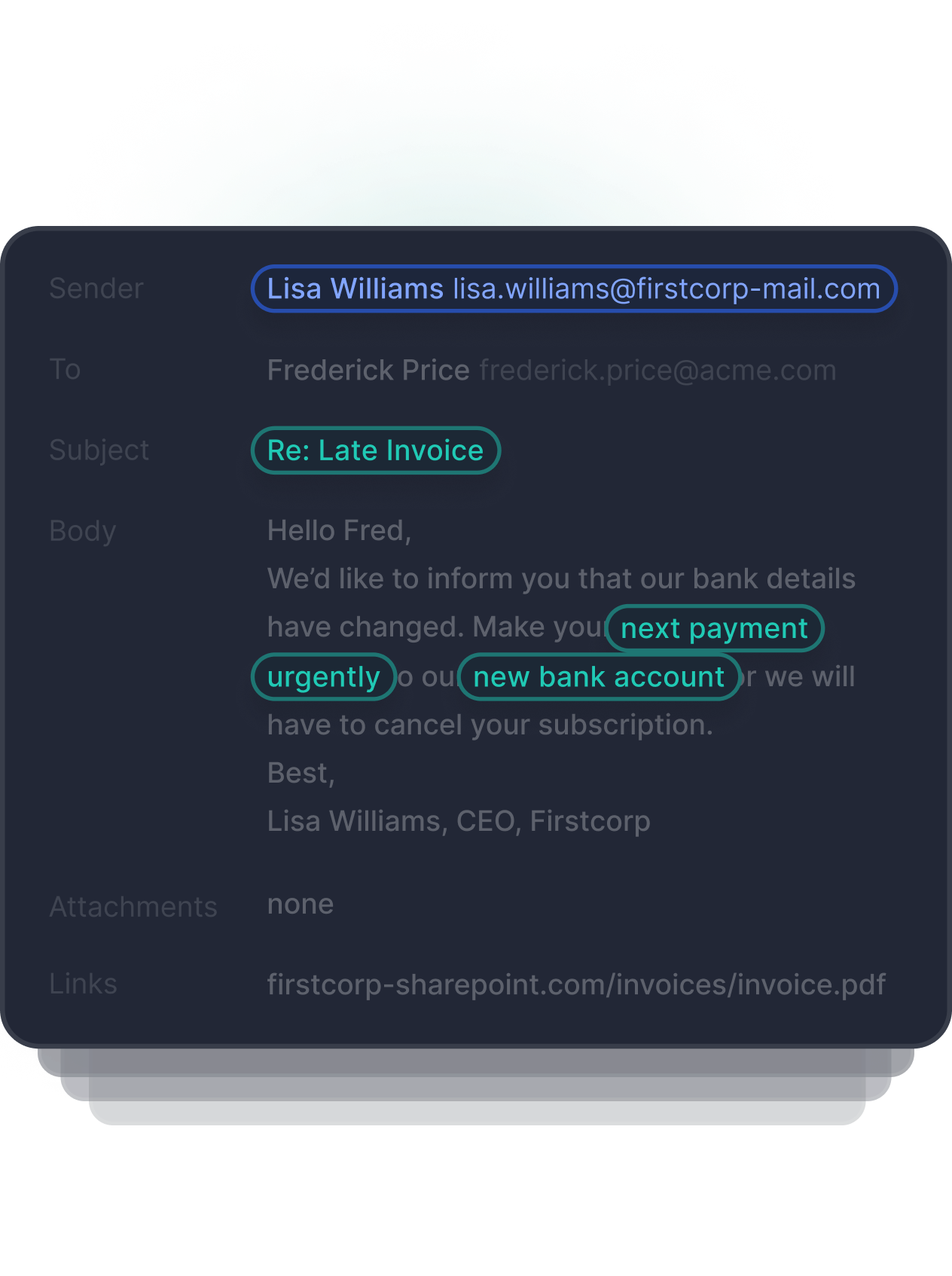
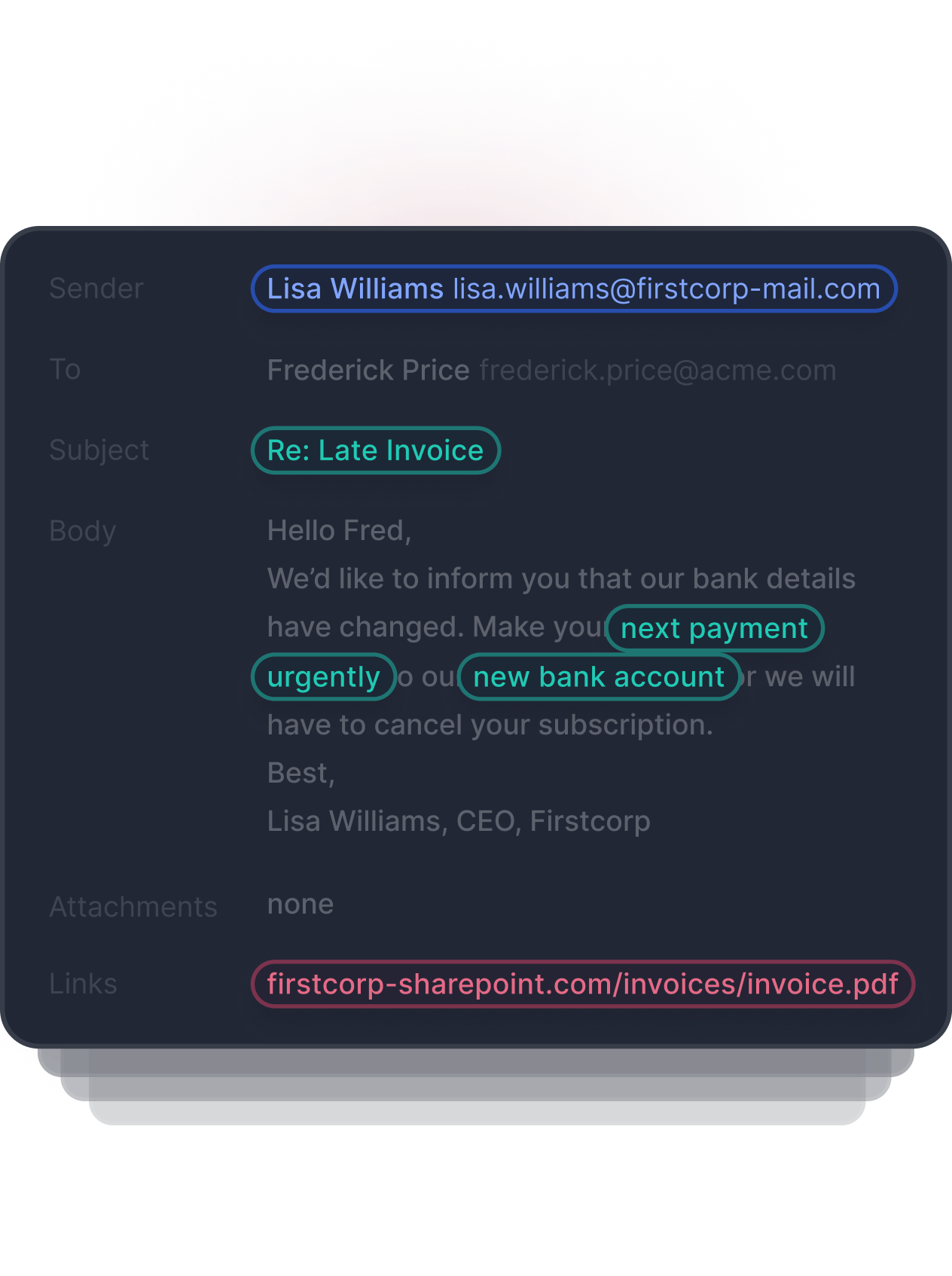
Content Analysis
Tessian’s machine learning identifies threats in image-based text, QR codes, URLs, subject headings, body text, and inside of email attachments. Hundreds of data points within each email are used to determine if the email is safe, malicious, or needs review.
Threat Network Analysis
The Tessian platform uses a global threat library to improve security across the network. Within minutes, Tessian adds malicious domains, urls, IPs, email addresses and file hashes to prevent email based attacks across the entire Tessian community.
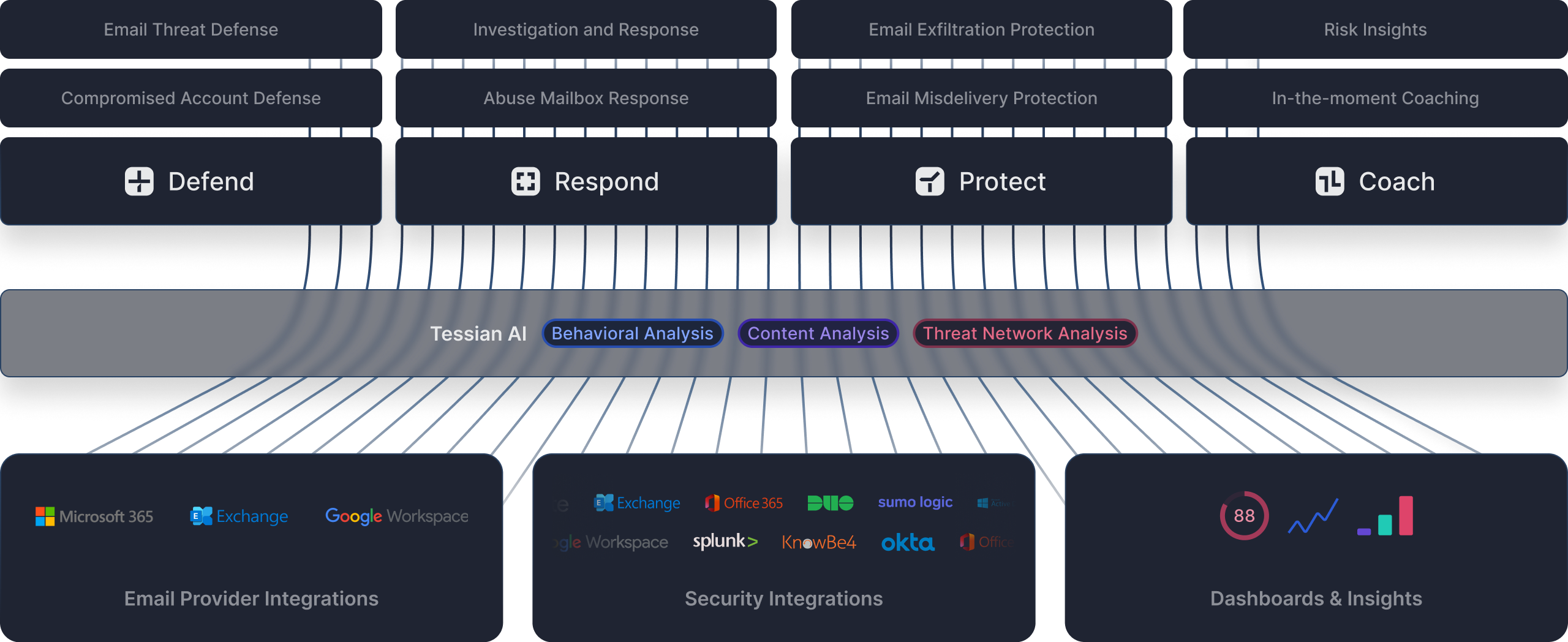
Complete cloud email security, deployed in minutes
Built to enhance Microsoft and Google email environments, Tessian is deployed in minutes through native API integrations with email providers.
Customer Stories
get in touch
See Tessian in Action
Book a personalized demo to see how Tessian defends against advanced phishing threats, and protects sensitive data on email.
Featured resources
-
Tessian + Microsoft 365
The rapid shift to a remote workforce has driven organizations towards cloud-hosted productivity suites and opened up a world of possibilities for seamless integrations with cloud security providers.Download Solutions Brief -

Forrester Consulting findings uncover a 268% ROI over three years with The Tessian Cloud Email Security Platform
This report dives into common challenges the interviewees faced and the reduction, efficiency, and organizational benefits enabled by Tessian.Download the Report